Most Common Passwords: Secrets & Security Risks You NEED To Know!
Are your online accounts truly secure? The alarming truth is that many of us are using passwords that are easily cracked, leaving our digital lives vulnerable to attack.
The realm of cybersecurity is constantly evolving, and one of the most fundamental aspects of online safety is the strength of your passwords. From the simplest social media accounts to the most sensitive financial information, the passwords we choose are the first line of defense against unauthorized access. Recent studies, such as those conducted by Nordpass, a password management tool, have repeatedly highlighted the pervasive use of weak passwords, exposing millions to potential breaches. Knowing the most common passwords and understanding why they are a risk is the first step in protecting yourself.
The data, meticulously compiled and analyzed, sheds light on the types of passwords that are most frequently employed, how hackers exploit these weaknesses, and the steps individuals can take to fortify their online security. Furthermore, we will explore the latest trends in password security, the best password managers available, and the importance of creating strong, unique passwords.
| Topic | Password Security |
| Description | A multifaceted topic that involves creating and managing passwords to protect online accounts and data from unauthorized access. |
| Key Characteristics |
|
| Risks |
|
| Best Practices |
|
| Future Trends |
|
| Relevant Websites | OWASP Top Ten |
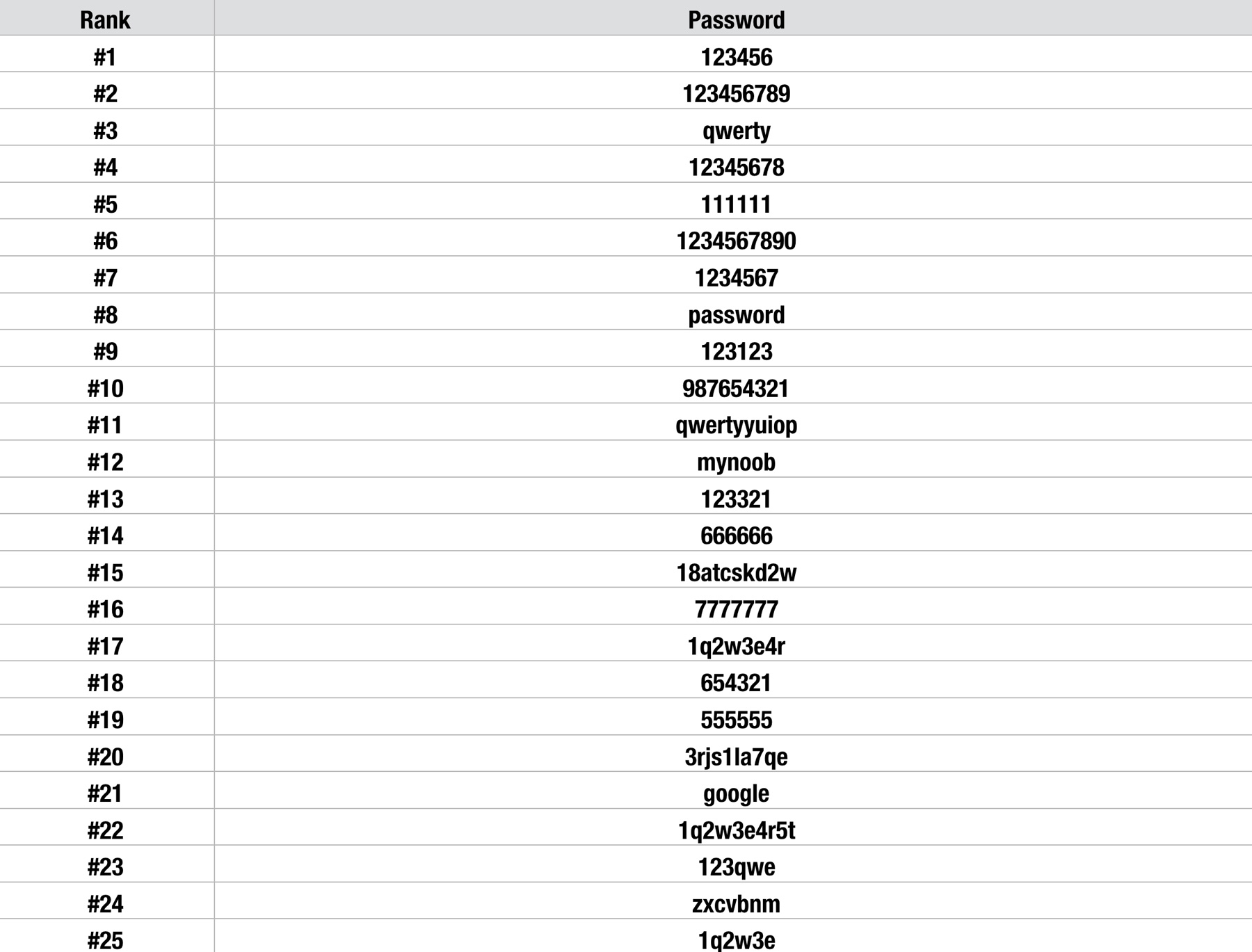
The "worst passwords" lists, often published annually by security firms like SplashData, provide a stark illustration of this problem. These lists are compiled from massive datasets of leaked passwords from data breaches, primarily in North America and Western Europe. By analyzing the most frequently used passwords, these firms highlight the patterns of user behavior that contribute to widespread vulnerability.
The lists themselves are often revealing. Frequently, the top ten most common passwords include variations of "123456," "password," "qwerty," and other easily guessable sequences. Nordpass's 2022 list, for example, indicated that "123456" remained the most common password, used millions of times globally. In 2023, the same trend continued, with "123456" still topping the charts, followed by "admin." This repeated presence of basic and predictable passwords underscores a fundamental lack of password security hygiene among a significant portion of internet users.
One aspect of these lists that often goes unnoticed, but is nonetheless crucial, is the presence of the 773rd most common password. While the exact password varies over time as password lists are updated, the very fact that a less-than-secure choice can rank so high on a list of common passwords shows how many people still opt for vulnerable options. This can be a wake-up call for those who might think a slightly more creative password offers sufficient protection. This highlights that even passwords that are slightly more complicated, but still based on personal information or easily guessable patterns, are insufficient in the face of determined attacks.
- Love On The Spectrum James Jones Love Story More Revealed
- Neela Jolene Actress Tiktok Star Rising Hollywood Talent
The methods hackers use to crack passwords are constantly evolving, but they often rely on some fundamental techniques. One common strategy involves using lists of common passwords, often obtained from compromised databases. Hackers will use automated tools that try these passwords against numerous accounts. If a user has chosen one of these common passwords, their account is swiftly compromised. Another technique involves brute-force attacks, where the system tries every possible combination of characters until the correct one is found. This can be a time-consuming process, but simple passwords can be cracked in a matter of seconds.
Nordpass's annual reports serve as a stark reminder of the ongoing challenges. The company's 2023 study, for instance, revealed that a significant number of users continue to rely on easily guessable passwords, demonstrating a persistent lack of imagination or awareness when creating credentials. The study examines a database containing a vast amount of leaked passwords, providing a clear picture of global password habits and their impact on security.
The frequency with which people reuse passwords is another significant vulnerability. More than six in ten people admit to reusing passwords across multiple accounts. While this may seem convenient, it creates a single point of failure. If one account is compromised, all accounts using the same password are also at risk. The use of pet names, birthdates, and other personal information in passwords is also common, making them easier for attackers to guess through social engineering or simple research. The combination of reusing passwords and using easily guessable information significantly increases the risk of account compromise.
The trends in password security are shifting. The future is moving toward passwordless authentication methods, such as biometric verification (fingerprint or facial recognition) and multi-factor authentication. Artificial intelligence (AI) is playing an increasing role in threat detection and password management, with AI-driven tools capable of identifying and mitigating potential breaches. The emphasis is also shifting towards educating users about cybersecurity best practices, which is essential for fostering a culture of online safety.
Creating strong passwords is a critical component of online safety. A strong password is a minimum of 12-16 characters long and includes a mix of uppercase and lowercase letters, numbers, and symbols. It should be unique for each account and never reused. It's important to avoid using personal information such as names, birthdays, or common words. Password managers are invaluable tools for generating, storing, and managing complex passwords. They can help users create strong passwords, remember them, and securely store them.
It is crucial to stay informed about cybersecurity threats. Hackers are constantly developing new techniques, so users must stay up-to-date with the latest risks. The most common password lists are a useful resource for understanding the types of passwords to avoid. Users should also enable two-factor authentication (2FA) on all accounts that support it. 2FA provides an extra layer of security by requiring a second verification method, such as a code sent to a phone, in addition to the password. Regular password updates, combined with these other measures, are essential for maintaining strong security practices.
Password leaks are a significant source of account compromise. These leaks happen when databases containing user credentials are breached. This can occur due to vulnerabilities in software, phishing attacks, or other means. The data contained in these breaches includes passwords, usernames, and other personal information. Countries like Russia, the United States, Canada, France, and Germany are often reported as locations where password leaks are most frequent. Understanding how and where these leaks happen is crucial for assessing risks and making informed decisions regarding account security.
When choosing a new password, consider the length. As seen in the data collected by Nordpass and others, the length of passwords directly impacts their security. The longer the password, the more secure it is. While the global top 200 passwords may range in length from 4 to 15 characters, the most common length for secure passwords is between 12 and 16 characters. This makes a significant difference in the time and effort required to crack a password. Passwords of the highest security should incorporate a random combination of letters, numbers, and symbols, making them nearly impossible to guess.
In conclusion, the password landscape presents a complex set of challenges and risks. Weak passwords and poor password management practices leave users vulnerable to cyberattacks, while the methods employed by hackers continue to evolve. By implementing the recommended practices, such as using strong passwords, enabling 2FA, employing password managers, staying informed about threats, and being wary of phishing attempts, individuals can significantly improve their online security. The future of password security involves a shift toward passwordless authentication, enhanced security measures, and increased user education, making it a dynamic and evolving field in the fight against cybercrime. As technology progresses, so too must our security practices, which requires constant attention and a commitment to best practices.
Article Recommendations


Detail Author:
- Name : Kavon Kshlerin
- Username : fahey.aliya
- Email : ckling@gmail.com
- Birthdate : 2005-12-12
- Address : 1187 Deckow Circles Apt. 747 Port Gilbertport, AL 23040
- Phone : 1-585-533-5987
- Company : Balistreri Group
- Job : Portable Power Tool Repairer
- Bio : Earum non dolor corporis possimus. Quia voluptatem laborum qui laudantium eius quia. Modi voluptatem inventore hic maxime voluptatibus aut eaque. Aut eaque ratione corrupti aliquid velit.
Socials
tiktok:
- url : https://tiktok.com/@katherine.zemlak
- username : katherine.zemlak
- bio : Qui voluptatem id id blanditiis. Explicabo et vel asperiores sunt mollitia.
- followers : 1949
- following : 442
linkedin:
- url : https://linkedin.com/in/zemlakk
- username : zemlakk
- bio : Assumenda saepe quia minus voluptate.
- followers : 4148
- following : 2511